Making Future Software Memory-Safe- A path towards Secure Cloud

On Feb 26, 2024, the White House Office of the National Cyber Director released a report asking the technical community to proactively reduce the attack surface in cyberspace. More research on this topic revealed that some of the most infamous cyber events that had grabbed headlines were the Heartbleed vulnerability (2014) and BLASTPASS exploit chain (2023), which caused real-world damage to the systems that society relies on daily.
Who would imagine that underlying these attacks was a common root cause: memory safety vulnerabilities, which have plagued the digital ecosystem for years. Now is the time to proactively eliminate memory safety bugs, which are the key component of software vulnerabilities. Memory safety vulnerabilities are a class of vulnerability impacting how memory is accessed, read/written, and allocated/deallocated in unintended ways. Surprisingly, with all the increased focus on software today, it is the programming languages such as C and C++ that have exhibited traits of being memory-unsafe languages.
Digging a bit deeper, memory safety violations fall into two categories: spatial safety and temporal safety. Spatial safety violation occurs when the memory is accessed outside of its bounds, such as buffer overflow. Temporal safety violation occurs when function pointer is overwritten with malicious data, forming the basis of several other attacks.
Continuing our path of innovation, the architectural team at Ampere has developed the means for improving security across the ecosystem through memory tagging. This powerful tool is available with AmpereOne® and specializes in detecting and mitigating buffer overflow security attacks and pointer programming errors. It is implemented in silicon hardware as a defense mechanism to detect both types of memory safety violations. This is performed before deployment by effective testing and at scale after deployment. It also increases robustness against violations such as rogue applications sniffing confidential user data or gaining unauthorized levels of system access.
How does Memory Tagging really work?
Memory Tagging provides memory management software capabilities to assign a unique 4-bit tag(lock) to every 16 bytes of memory and a tag (key) to the software (S/W) program pointer. Before the CPU can use data from memory or execute code, Memory Tagging ensures the program pointers tag matches the memory tag. If there is a mismatch between the pointers and the memory tag, the CPU causes a memory access fault, which prevents malicious code to execute.
In case of a buffer overflow attempting to overwrite critical control structures or code, incorrect memory tagging will prevent program execution or corruption of the data structures.
In case of use-after-free related exploits that manipulate pointers to freed (deallocated) memory for malicious purposes, memory management software changes the tag when memory is freed, so that any attempt to use the old pointer with the incorrect tag is blocked by Memory Tagging.
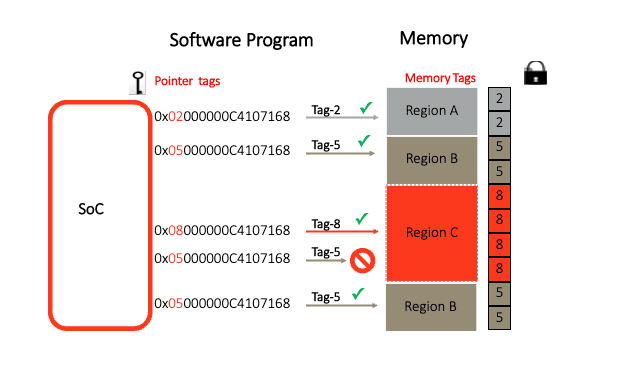
Customers can use it for probabilistic detection of random bad pointers and for guaranteed detection of sequential buffer overrun, where the allocator ensures adjacent blocks use different tags.
At Ampere, we focus on product high performance, and the same applies here. Our goal is to perform precise tag checking with minimal performance impact. With co-located tags and data, there is no memory space/bandwidth overhead and it is suitable for production deployment.
Memory Tagging is not simply a debugging feature that makes developers’ lives easier
Memory Tagging is much more than a debugging feature; it is a way for cloud users to experience higher levels of protection against memory attacks from inside or outside of cloud service providers (CSPs) infrastructure. With the confidence of enabling highly available secure applications, CSPs can offer their services (IaaS, PaaS) at higher margins to their customers or end users.
When users are ready to enable Memory Tagging, they must enable the NVPARAM feature in the firmware (or BIOS). Memory Tagging is supported throughout the SOC (core, mesh, SLC, memory controller) and is supported in Linux, gcc/glibc, gdb, and tools (ptrace etc.).
To see Memory Tagging in action, check our roadmap video:https://www.youtube.com/Memory Tagging
Stay tuned for more blogs on the unique features of AmpereOne.
